As 2021 winds to a close, security leaders can look back at a year that saw everything from supply chain attacks to a ransomware infection disrupting an American oil pipeline system. Hovering over this threat landscape is the COVID-19 pandemic, which forced many employees to work remotely and put pressure on organizations to examine and adjust their security strategies to support them. A lot more organizations are coming to a harsh realization that whether you’re a digital cyber-focused company or not, digital transformation has led to cybersecurity being part of each and every one of our worlds.
One of the most fundamental lessons to be learned in 2021 is that security deserves its place at the table when it comes time for business leaders to discuss their priorities. From the onboarding and offboarding of employees to protecting and managing the supply chain, cybersecurity touches essentially every aspect of business operations in some way. Supporting business objectives means weaving security into each and every business process and department.
In the last 12 months, there has been a 65% increase in security services. The global market for managed cybersecurity services is expected to grow to $46.4 billion by 2025 and 77% of cybersecurity spending will go to managed services by 2026. Organizations expect their MSP to keep up with the changing cybersecurity ecosystem at scale to fulfill their cybersecurity requirements and ensure the technology they have in place will protect them and their data.
The Human Firewall
Malicious actors are well aware that an established MSP typically handles significant volumes of sensitive client information. It’s crucial that MSPs keep both their own employees and their client’s employees well versed in cybersecurity best practices to ensure optimal security for their systems, along with their clients’ valuable data. MSPs need to ensure all of their clients’ employees are cyber aware whereas individual organizations only have to be concerned about their own employees.
Done right, cybersecurity awareness training turns humans into security multipliers. This effect is often referred to as the human firewall. Erecting these human defenses means identifying the most pressing risks to your clients and establishing a program that communicates the best practices for addressing them.
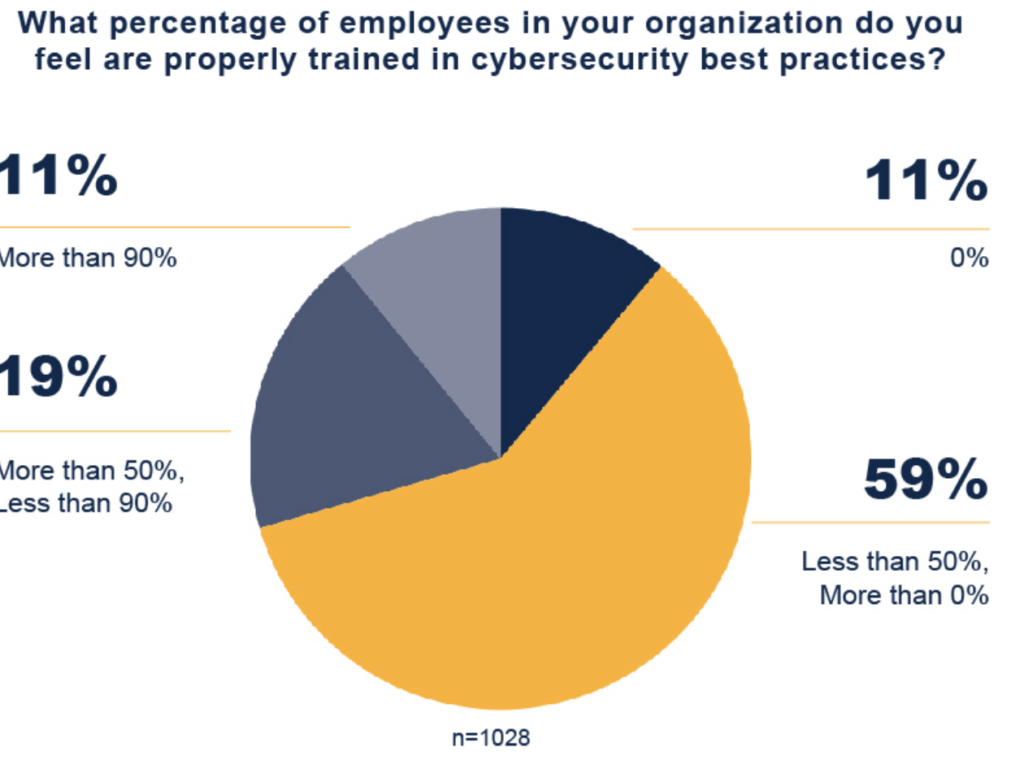
Cybersecurity is not a one-person operation; it is a team sport. A culture of cybersecurity in an organization includes all employees knowing how to protect themselves and the business from online threats.
The Cybersecurity Skills Gap
Part of the value in engaging with an MSP is that they can take advantage of economies of scale by standardizing a lot of the cybersecurity hygiene practices. However, similar to every other organization, MSPs are not immune to the ongoing cybersecurity skills gap. The success of an MSP depends on its ability to attract qualified employees. MSPs need flexible talent that can morph and shift with the changing needs of multiple clients all at once.
Cybersecurity is a relatively new career field, so we’re still seeing job standards evolve. There’s a fair bit of work to do in terms of raising awareness around cybersecurity in order to bridge the skills gap and address the lack of diversity in the talent pool. Additionally, almost every MSP is managing a remote workforce, whether they ever planned to or not. In a remote work environment, hiring and managing remote employees requires a high level of trust and confidence in their ability to work safely and adhere to cybersecurity processes. MSPs must become savvier with how they fill cybersecurity jobs. Recruiters who recycle the same ways of finding talent will miss qualified people and end up hiring people who resemble the team they already have. While cybersecurity experts are few and far between, there are non-traditional channels that could provide security teams with employees who can quickly be trained in cybersecurity, and perhaps diversify the skills on your team.
Between the skilled worker shortage, lack of cybersecurity awareness across organizations, and the complexity of the cybersecurity threat landscape, it’s clear people alone aren’t going to be enough to combat cybersecurity threats. MSPs must adapt and apply the right mixture of people, processes, and technology to enhance their security posture and offer better security services to clients.
Modernize Your Tech Stack
When you talk about IoT, hybrid workforce, etc – the whole human factor and its relationship with the Internet is a security and threat vector to appreciate. It doesn’t fit into the traditional cybersecurity threat landscape that many people think about, but it’s an emerging vector that organizations need to comprehend when they’re building out their policies. As with all of your defenses, up-to-date information about the threat landscape is a must for effectively guiding security awareness efforts and expanding your security service offering.
Threat intelligence provides the data that organizations need to inform their security strategy and identify emerging and ongoing threats towards their clients. This information does not just include stolen data or passwords but also negative mentions of corporate brands and information about third-party vendors, allowing you to make informed decisions across each client and business process. As an example, threat intelligence can provide information about unpatched vulnerabilities that organizations can consider alongside CVSS scores when deciding what issues to prioritize. Likewise, information about existing and prospective vendors might be of interest to the CISO.
While threat intelligence management is just one aspect of security, the ability to leverage that data effectively speeds up investigations and makes the process of detecting and responding to emerging and ongoing risks less burdensome for MSPs. With the need outpacing the supply, every bit helps.
Automation Saves the Day
The Internet isn’t like normal communication – it’s unstructured so there’s a lot of risk, complexity, and if you’re doing it manually, costs to get something intelligent out of it from a risk and threat lens. Organizations looking to handle the collection, correlation, and propagation of threat intelligence manually are in for a challenge, and it’s happening more often than you may think. Fifty percent of security practitioners use 100+ manual searches and spreadsheets in their workflow and 85% have received little or no training in OSINT techniques and risk prevention from their employer. When it comes to threat intelligence, it is unrealistic to think of a team of individuals manually searching the deep, dark, and surface web, Information Sharing and Analysis Centers (ISACs) and both commercial and free intelligence feeds. It is simply too much ground to cover, and that is before considering the actual processing of the information being gathered. The shortage of skilled cybersecurity analysts exacerbates this situation. To fill this need, organizations need the ability to automate the collection and triage of intelligence information throughout their security infrastructure.
Automating repetitive and mundane security tasks decreases human error in identifying potential threats and reduces the workload by limiting the number of tasks that need to be done manually. Increasing the speed of everyday tasks gives MSPs more time for other activities – ultimately leading to faster, smarter decisions.
“While threat intelligence management is just one aspect of security, the ability to leverage that data effectively speeds up investigations and makes the process of detecting and responding to emerging and ongoing risks less burdensome for MSPs. With the need outpacing the supply, every bit helps.”
Maximize Time to Value with Media Sonar
Media Sonar improves the operational efficiency of analysts and increases ROI on existing solutions by consolidating indicators of threat from the surface, deep and dark web. Our cloud-based platform will broaden your lens on your client’s digital attack surface – helping you to secure your client’s brand and assets and strengthen your security operations posture. Keep up with the changing cybersecurity ecosystem and better protect a number of assets for a number of clients by reducing the risk, complexity, and cost associated with the ever-increasing threat landscape found in web channels.